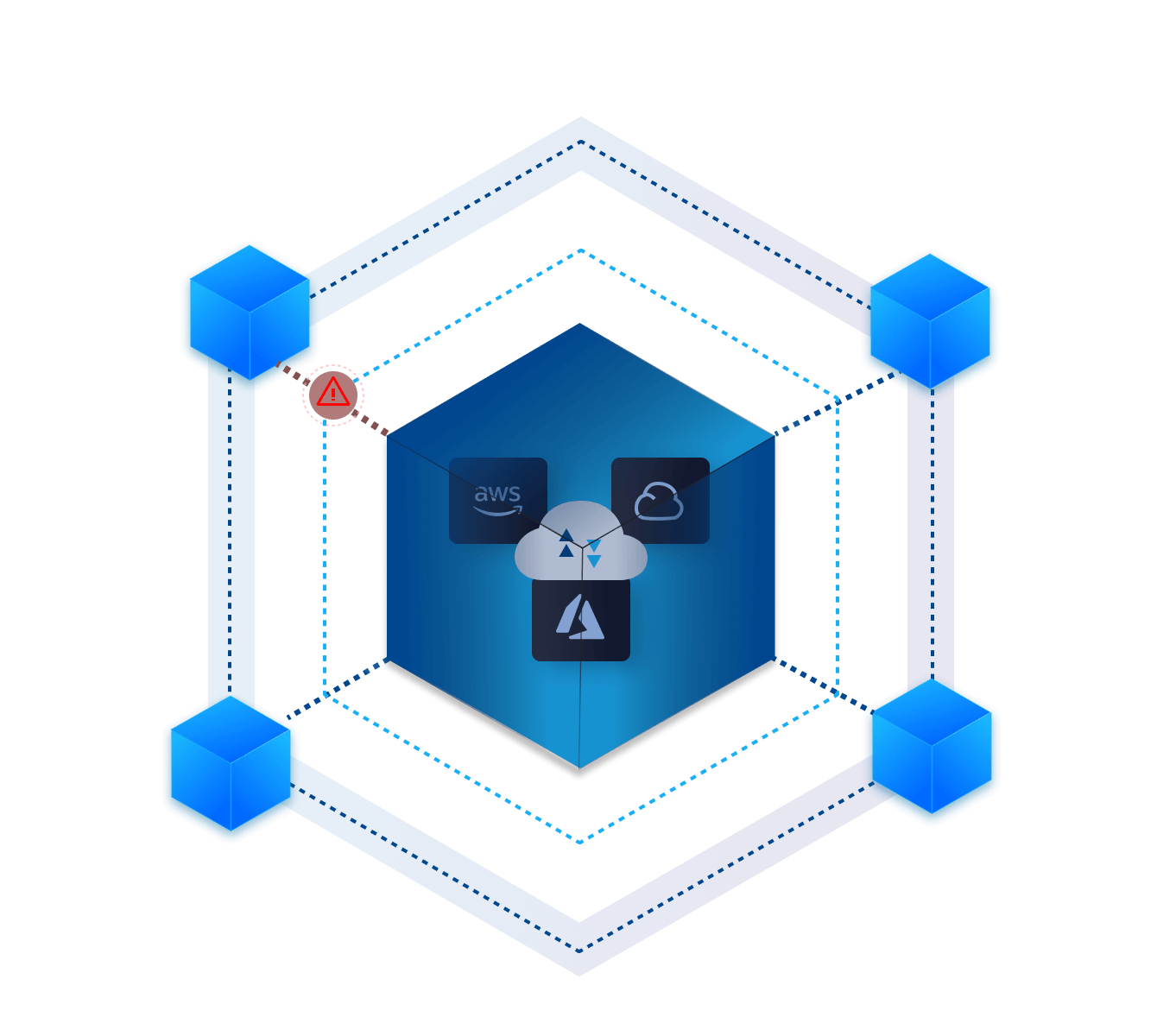
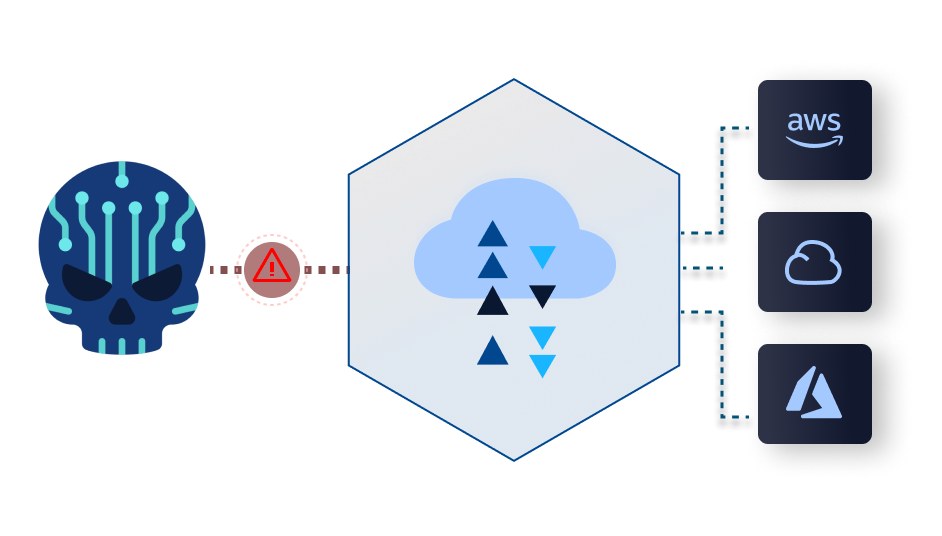
Working on the cloud offers unrivaled benefits, flexibility, and competitive advantages. However, with such freedoms comes increased security risks. Any application, service, container, or database running in the cloud is a cloud workload. Protecting your cloud workloads should be a top priority to ensure smooth day-to-day operations and avoid costly breaches.
What Is Cloud Workload Protection (CWP)?
Cloud workload protection (CWP) is the act of continually monitoring cloud workloads and containers and removing threats or addressing vulnerabilities.
A Cloud Workload Protection Platform (CWPP) is a security solution to safeguard any workload in any location. You’ll get complete visibility and frictionless security with a unified cloud workload protection solution across multiple providers.
In some cases, CWPP integrates with cloud security posture management (CSPM). While CWP ensures the security of cloud workloads, CSPM focuses on the bigger picture, such as accounts accessing cloud platforms.
How Does A CWPP Work?
CWPPs can manage the real-time security of any workload across your cloud platforms. Typically, network administrators assess vulnerabilities, compliance protocols, and cybersecurity policies across the workload. If necessary, the admin manually applies security techniques, such as integrity or memory protection, allow lists, host-based intrusion protection, and anti-malware protection.
Much of these manual security techniques can be automated with CWPPs including both behavior-based and file-based security protections built for cloud workloads.
Why Is CWP Important?
Working with the cloud is essential for any modern-day business. To stay competitive, companies must take advantage of the latest technologies.
Cloud platforms are vital drivers for digital transformation and growth. Migrating to the cloud can help deliver better quality services more efficiently. Moreover, the cloud allows for greater speeds and scalability than traditional technology.
However, relying on a cloud environment means protecting your workloads from an increasingly large attack surface. From cloud workloads to virtual servers, cloud security is essential.
Cloud workload protection (CWP) offers breach protection while enhancing your organization’s growth.
Benefits of CWP
How can CWP protect your business’ cloud infrastructure and workload?
Protection
CWP secures your cloud environment, including your entire cloud stack, on any cloud and any workload across containers and Kubernetes applications. With automated security and threat detection, cloud workload protection will stop suspicious activity without causing alert fatigue.
Frictionless
A cloud workload protection platform supports continuous integration and continuous delivery workflows. As DevOps moves faster and becomes more advanced, you don’t need to leave your security protocols behind. CWPP allows you to secure workloads at the speed of DevOps without sacrificing security or performance.

Cloud Workload Security Challenges
Cloud computing is dynamic. However, relying on a cloud environment means enhancing security measures around all workloads and endpoints. The unique characteristics and capabilities of cloud technology create new security challenges.
Expanded Attack Surface
While cloud software allows users to access your systems and instances anywhere in the world, off-premise locations mean higher risk and an expanded attack surface.
With cloud technology, you need to secure virtual servers, remote applications, cloud workloads, containers, and network communications. More users, with varying security expertise, in different locations also pose a risk.
Visibility
Blind spots are the biggest downfall for many businesses. Without complete visibility, you won’t notice potential risks of vulnerabilities before they become breaches. Traditional security tools are not up to scratch. Moreover, containers are short-lived—making data collection and incident investigation difficult.
Performance
While cloud workloads and containers are highly dynamic, they pose more significant security challenges. Traditional solutions and processes are no longer sufficient. As cloud workloads allow rapid deployment and scaling, your attack surface continuously changes. Security solutions must match the speed of DevOps without limiting or sacrificing performance.
Key Requirements of Cloud Workload Protection Platform
Featured Partners
Falcon Cloud Workload Protection provides comprehensive protection against breaches and threats across private, public, hybrid, and multi-cloud environments. You can rapidly adapt and secure cloud technology across your workloads with Falcon.

Prisma Cloud secures hosts, containers, and serverless applications throughout your cloud workload ecosystem. With unique security approaches to each container. Prisma Cloud evolves with diverse architectures to offer complete protection.

Featured Cloud Workload Protection Partners:
Defensive Cloud Workload Protection – Featured Partner Solutions
What cloud workload protection solutions can we offer to take your security to the next level?
Why Defensive Networks?
Defensive is a Next Generation Solution Provider for a Cloud-First World. We exist to take the guesswork out of Cybersecurity and Information Technology procurement and adoption.
Defensive of your Brand.
We are trusted by leading enterprises around the globe.
Defensive of your People.
Let’s create harmony between Infosec, IT, Executives, End Users, and Finance.
Defensive of your Time.
We’re straight to the point with technologies and strategies that work.
Defensive of your Budget.
Eliminate wasted expenditure and maximize the value of every dollar.
TRUSTED BY
87 of the Fortune 1000
Over 1,400+ small, medium and large enterprises.









As Seen In
Defensive Cloud Workload Protection
Identity is the foundation of a modern security program, and as such, we partner with the best. We use technologies from Okta, Microsoft, and CrowdStrike to create a fool-proof access management solution. With an IAM system, your organization will see increased security and productivity. We use real-time threat detection, prevention, and valuable analytics that produce actionable insights to enhance your organization’s security.

Cloud Workload Protection
Cloud Native Security
Powered By DEFENSIVE