Gone are the days of huddling behind a firewall and securing the network with MAC addresses, ACLs, and NACs. Digital Transformation moved businesses to the cloud, and network security must adapt to this new cloud era.
Zero Trust 2.0
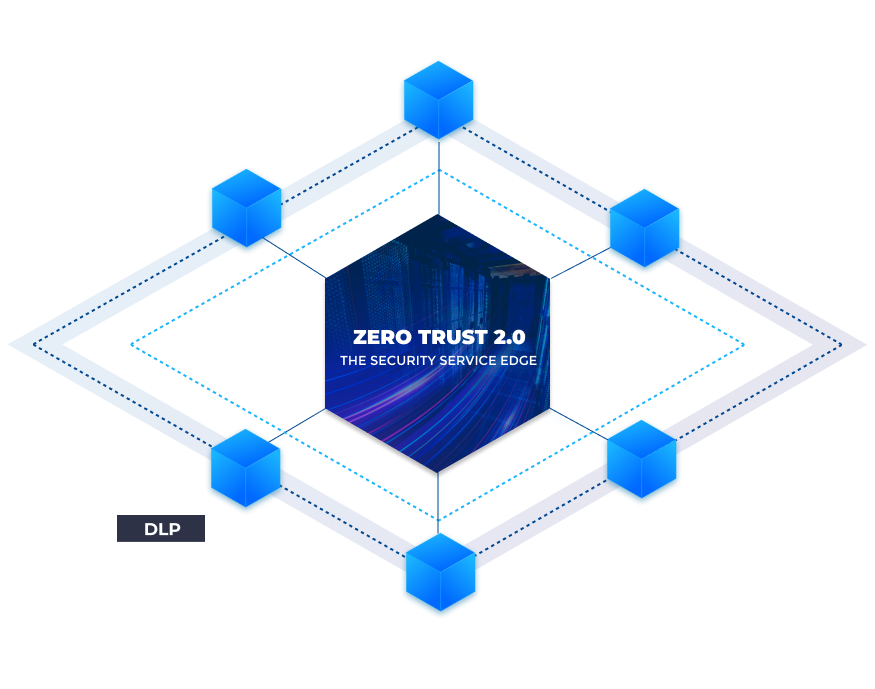
Security Service Edge (SSE)
Enter Zero Trust 2.0, Powered by Security Service Edge technologies. Gartner defines Security Service Edge (SSE) as secured access to the web, cloud services, and private applications.
What Is Zero Trust 2.0?
Zero Trust is a strategic cybersecurity approach to eliminate any and all cyber threats. It sits on top of a modern Identity Access Management (IAM) solution to create an airtight security strategy by eliminating implicit Trust and continuously interrogating and validating every digital interaction- be it on-premise, private cloud, public cloud, or Software as a Service (SaaS). Zero Trust protects all users, devices, applications, and data.
What does Zero Trust mean?

Transform IT and Security
We’ll help you transform your business for the modern age. Security becomes more complicated with a mix of remote, in-office, and hybrid working taking over traditional business practices. We’ll help you move away from legacy network architecture to a more secure cloud-based system with the principles of Zero Trust.
Defensive SSE solutions can address evolving threats and new risks. We’ll handle technology shifts, organizational changes, and new compliance requirements, whichever industry you’re in.
Modernized Private Access
Like a firewall of all things in all places, Zscaler is a cloud security platform that provides speedy and secure connections between applications. Using the Zero Trust principles, our solutions determine appropriate access levels and restrictions to keep users, applications, and data safe.
Next Generation ZTNA solutions connect users, applications, and hardware over any network and any location.
“I love using my VPN” – No End User, ever
Ditch the legacy dial-up VPN for a modernized approach to more securely accessing your applications, wherever they are.

The Zero Trust Exchange terminates each connection to inspect and verify it before allowing the appropriate level of access to prevent superficial external and lateral cyber threats.

Zero Trust 2.0 is built off a strong IAM foundation
Zero Trust 2.0 requires a strong foundation of an adaptive Identity platform. We enhance our Zero Trust solutions with strong Privilege Access Management, Entitlement Access Management, and Adaptive MFA to support our cloud-based security. Entitlement management provides a way to control access and user privileges within a system.
You can grant appropriate access levels from one portal, while multi-factor authentication ensures the user is who they say they are.
With two levels of identity access management, we can prevent surface-level threats from becoming severe breaches.
Featured Zero Trust Partners
How Do We Protect Your Users and Your Data?
We utilize top-of-the-range security technologies and Software to keep your systems safe. Each protocol works together to prevent all kinds of attacks across your applications and network.
CASB
A CASB (cloud access security broker) is a gatekeeper between users and applications. They allow organizations to extend security policies beyond their own infrastructure with firewalls to identify and prevent malware.
A CASB also enforces authentication, single sign-on, authorization, credential mapping, device profiling, encryption, logging, and alerting.
Cloud NGFW
Cloud NGFW (next-generation firewall) is an industry-leading network security that stops highly sophisticated threats in real time. Cloud NFGW is part of the next generation of firewall technology to detect and block attacks by enforcing security in applications and at port and protocol levels.
Cloud NGFW includes application control, integrated intrusion prevention, and cloud threat intelligence.
SWG
A secure web gateway (SWG) protects users from web-based threats by applying and enforcing security policies. An SWG solution offers broader protection than CASBs, as it blocks access to or from malicious websites and links by filtering web traffic.
WAF
A web application firewall (WAF) monitors, filters, and blocks data traveling to and from a website or application. A WAF can work on a cloud-based system. A WAF protects against vulnerabilities by filtering malicious traffic—it’s essential for your system security because of the speed and ease of modifying policies to respond to attacks more quickly.
DLP
Data loss protection (DLP) includes a set of technologies and techniques to ensure you don’t lose sensitive or crucial data or unauthorized user access and misuse of your information. DLP software classifies confidential business data and identifies violations of security policies. It alerts, encrypts, and offers other protective actions to prevent end users from sharing data.
Zero Trust Private Access
Zero Trust assumes that every access request is a potential threat and examines each connection before granting access. A Zero Trust network access (ZTNA) enables secure access to internal applications for remote users while identifying and removing unauthorized users. Trust is never implicit, with access granted on a need-to-know basis.
Principle of Least Privilege
The Principle of Least Privilege only allows users to access essential applications and data to complete the task. In other words, you only get the privileges you need for your job role—no more, no less. If users do not need access, they do not have it. The Principle of Least Privilege prevents accidental or malicious data breaches at the surface level.
Zero Trust 2.0 Features

Why Defensive Networks?
Defensive is a Next Generation Solution Provider for a Cloud-First World. We exist to take the guesswork out of Cybersecurity and Information Technology procurement and adoption.
Defensive of your Brand.
We are trusted by leading enterprises around the globe.
Defensive of your People.
Let’s create harmony between Infosec, IT, Executives, End Users, and Finance.
Defensive of your Time.
We’re straight to the point with technologies and strategies that work.
Defensive of your Budget.
Eliminate wasted expenditure and maximize the value of every dollar.
TRUSTED BY
87 of the Fortune 1000
Over 1,400+ small, medium and large enterprises.









As Seen In
Defensive Zero Trust 2.0
A Zero Trust approach will prevent accidental and malicious breaches before they occur. We can tighten your access points and vulnerabilities with simple but effective solutions to ensure only the right people access the right applications.
Whether you work remotely, in the office, or with a hybrid approach, our Defensive Zero Trust 2.0 solution can save you from the worst-case scenario—by assuming that every scenario is the worst case.

Zero Trust Network Access
Zero Trust
Powered By DEFENSIVE