Business Email Compromise and Vendor Email Compromise attacks have been the most prolific increase in cyber-attack vectors over the last few years. It seems that every organization we’ve talked to has one or more stories about paying fraudulent invoices, or the classic last minute request from the CEO to fill up gift cards for an event.
In a BEC attack, the attacker gains access to an employee’s email account and uses it to send fraudulent emails to other employees or vendors in the organization. The emails may request payments or transfers of funds to bank accounts controlled by the attacker, or may contain malware or phishing links to steal sensitive information.
In a VEC attack, the attacker gains access to a vendor’s email account and uses it to send fraudulent emails to the organization. The emails may request payments or transfers of funds to bank accounts controlled by the attacker, or may contain malware or phishing links to steal sensitive information.
BEC and VEC attacks can happen in several ways, including:
Phishing: Attackers may use phishing emails to trick employees or vendors into providing their login credentials or clicking on malicious links, allowing them to gain access to email accounts.
Social Engineering: Attackers may use social engineering techniques to gather information about employees or vendors, such as their email addresses and job titles, which can be used to craft convincing fraudulent emails.
Malware: Attackers may use malware to gain access to email accounts and monitor email traffic, allowing them to identify targets for fraudulent activities.
Compromised Credentials: Attackers may use stolen login credentials to gain access to email accounts, either through brute-force attacks or by purchasing them on the dark web.
Recommendations for protecting your organization from BEC and VEC attacks:
To protect against BEC and VEC attacks, organizations should implement email security solutions that use advanced threat protection (we recommend ICES platforms in most cases), user awareness training, and continuous monitoring and analysis of email traffic. Organizations should also enforce strong authentication and access control measures for email accounts, regularly review and update their security policies, and implement multi-factor authentication to protect against compromised credentials.
Large-scale BEC and VEC attacks in the news:
There have been several large-scale BEC and VEC attacks in the last couple of years, resulting in significant financial losses for the affected organizations. Here are some of the most notable examples:
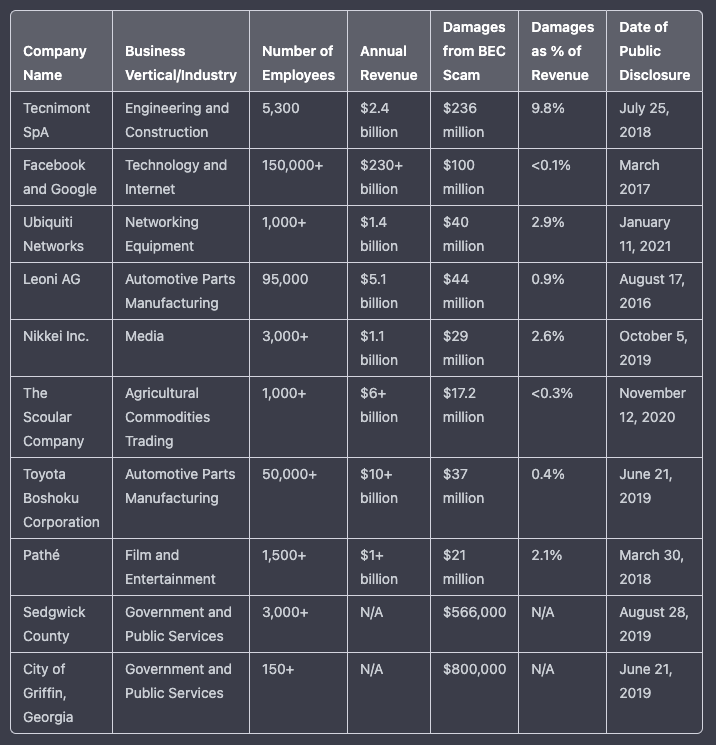
Nikkei Inc.: In September 2019, Nikkei Inc., a major Japanese media company, was the victim of a BEC attack that resulted in a loss of $29 million. The attackers had gained access to an employee’s email account and used it to send fraudulent payment requests to a subsidiary of the company.
Toyota Boshoku Corporation: In August 2019, Toyota Boshoku Corporation, a major Japanese automotive parts manufacturer, was the victim of a VEC attack that resulted in a loss of $37 million. The attackers had gained access to a vendor’s email account and used it to send fraudulent payment requests to the company.
State of Texas: In 2018, the State of Texas was targeted in a series of BEC attacks that resulted in losses of over $2 million. The attacks involved compromised email accounts of vendors and involved fraudulent payment requests to the state.
Save the Children Federation: In April 2019, the Save the Children Federation was targeted in a VEC attack that resulted in a loss of $1 million. The attackers had gained access to a vendor’s email account and used it to send fraudulent payment requests to the organization.
City of Griffin, Georgia: In March 2021, the City of Griffin, Georgia was targeted in a VEC attack that resulted in a loss of $800,000. The attackers had gained access to a vendor’s email account and used it to send fraudulent payment requests to the city.
Ubiquiti Networks: In January 2021, Ubiquiti Networks, a major networking equipment vendor, disclosed that it had been the victim of a BEC attack. The attackers had gained access to an employee’s email account and used it to send fraudulent emails to vendors requesting changes to their payment information. The attackers were able to redirect payments to their own bank accounts, resulting in losses of over $40 million.
City of Ocala: In July 2020, the City of Ocala in Florida was targeted in a VEC attack. The attackers had gained access to a vendor’s email account and used it to send fraudulent emails to the city’s finance department, requesting payments to a fraudulent bank account. The city lost over $742,000 as a result of the attack.
These attacks typically involve social engineering, phishing, and other tactics designed to trick employees or vendors into disclosing login credentials or other sensitive information. To prevent these types of attacks, organizations should implement security measures such as multi-factor authentication, email filtering and monitoring, and user awareness training. Additionally, it is important to establish clear policies and procedures for verifying payment requests and other sensitive information, and to regularly review and update these policies to stay ahead of evolving threats.

The top 10 BEC or VEC attacks in order of largest damages incurred are:
- BEC scam against Tecnimont SpA: $236 million in losses
- VEC scam against Facebook and Google: $100 million in losses
- BEC scam against Ubiquiti Networks: $40 million in losses
- BEC scam against Leoni AG: $44 million in losses
- VEC scam against Nikkei Inc.: $29 million in losses
- BEC scam against The Scoular Company: $17.2 million in losses
- BEC scam against Toyota Boshoku Corporation: $37 million in losses
- BEC scam against Pathé: $21 million in losses
- BEC scam against Sedgwick County: $566,000 in losses
- BEC scam against City of Griffin, Georgia: $800,000 in losses
Table:
Double Clicking into the VEC attacks against Google and Facebook
In March 2017, it was reported that a Lithuanian man named Evaldas Rimasauskas had scammed Google and Facebook out of $100 million in a VEC attack. Rimasauskas had set up a fake company called Quanta Computer, which had the same name as a legitimate Taiwanese hardware manufacturer, and used it to send fraudulent invoices and payment requests to Google and Facebook.
Rimasauskas had created fake email accounts and documentation to make it appear as though the invoices and payment requests were legitimate. He had also impersonated Quanta Computer executives to provide further credibility to his requests. The fraudulent invoices and payment requests were then approved and paid by Google and Facebook, resulting in the loss of $23 million from Google and $99 million from Facebook.
The scam was uncovered when a bank in Latvia raised concerns about the large volume of funds being transferred to accounts associated with Rimasauskas. The U.S. Department of Justice subsequently charged Rimasauskas with wire fraud, money laundering, and aggravated identity theft. In March 2019, Rimasauskas pled guilty to the charges and agreed to forfeit $49.7 million in proceeds from the scheme.
The VEC scam against Google and Facebook highlights the importance of strong vendor management practices and the need to verify payment requests from vendors before processing them. It is also a reminder of the importance of implementing security measures such as multi-factor authentication, email filtering and monitoring, and user awareness training to prevent these types of attacks.
Double Clicking into the VEC scam against Ubiquiti
In 2021, Ubiquiti Networks, a major networking equipment vendor, disclosed that it had been the victim of a Vendor Email Compromise (VEC) attack that resulted in a loss of over $40 million. The attackers had gained access to an employee’s email account and used it to send fraudulent emails to Ubiquiti’s finance department and external vendors.
The fraudulent emails contained requests for changes to vendor payment information and bank accounts, directing the payments to bank accounts controlled by the attackers. The attackers were able to redirect multiple payments over a period of several months, resulting in the significant financial loss to the company.
The attackers were sophisticated and used tactics such as social engineering and spear-phishing to gain access to the employee’s email account. They also had knowledge of Ubiquiti’s internal procedures and systems, which allowed them to conduct the fraud without detection for an extended period.
Ubiquiti responded to the attack by resetting all employee passwords and implementing multi-factor authentication for remote access to the company’s systems. They also conducted a comprehensive investigation into the attack and reported it to the authorities.
This VEC scam against Ubiquiti highlights the importance of strong cybersecurity measures and awareness training for employees and vendors. It also underscores the need for organizations to conduct regular risk assessments and implement measures such as multi-factor authentication, encryption, and access controls to protect against email-based attacks.
Double Clicking into the VEC scam against Toyota
In August 2019, Toyota Boshoku Corporation, a major Japanese automotive parts manufacturer and supplier to Toyota Motor Corporation, was the victim of a Vendor Email Compromise (VEC) scam that resulted in a loss of $37 million. The attack involved compromised email accounts of one of Toyota Boshoku’s foreign subsidiaries and an associated vendor.
The attackers had gained access to the vendor’s email account and used it to send fraudulent payment requests to Toyota Boshoku, directing the payments to bank accounts controlled by the attackers. The fraudulent emails were sent over a period of several months, and the payments were approved by Toyota Boshoku’s finance department without suspicion, as they appeared to be legitimate requests from a trusted vendor.
The scam was discovered when the vendor noticed the fraudulent bank account details in the payment requests and alerted Toyota Boshoku. Toyota Boshoku subsequently reported the incident to the authorities and launched an investigation.
The VEC scam against Toyota Boshoku highlights the importance of strong vendor management practices and the need to verify payment requests from vendors before processing them. It also emphasizes the need for organizations to implement security measures such as multi-factor authentication, email filtering and monitoring, and user awareness training to prevent these types of attacks.
In response to the attack, Toyota Boshoku announced that it would be implementing stronger authentication and authorization controls, as well as conducting regular training for employees and vendors on how to recognize and respond to email-based attacks. Additionally, Toyota Boshoku emphasized the importance of sharing information and best practices with other companies in the supply chain to help prevent similar attacks in the future.
Double Clicking into the Tecnimont SpA scam
In 2018, Tecnimont SpA, an Italian engineering and construction company, was the victim of a Business Email Compromise (BEC) scam that resulted in a loss of $236 million. The attack involved compromised email accounts of Tecnimont’s management and staff.
The attackers had used social engineering tactics, such as spear-phishing emails, to gain access to Tecnimont’s email accounts. They then used the compromised accounts to send fraudulent emails to Tecnimont’s finance department, requesting large transfers of funds to bank accounts controlled by the attackers.
The fraudulent emails appeared to be legitimate requests from senior executives, and the transfers were approved by the finance department without suspicion. The attackers were able to transfer the funds to accounts in various countries, making it difficult to recover the stolen funds.
The scam was discovered when the company’s bank raised concerns about the large transfers, and an internal investigation revealed the fraudulent activities. Tecnimont subsequently reported the incident to the authorities and launched a legal action against the banks involved in the transfer of funds.
The BEC scam against Tecnimont is one of the largest known cyber fraud incidents in history. It highlights the importance of strong cybersecurity measures, including multi-factor authentication, email filtering, and user awareness training, to prevent email-based attacks. It also underscores the need for organizations to verify payment requests from senior executives and to implement internal controls to prevent large transfers of funds without proper authorization.
Protecting your organization against these advanced attacks requires a defense in depth strategy, along with a next gen email security platform.
Let’s connect and show you how we can help you protect your organization
